Home Assistant and the smart devices that connect to your home network are always at risk of being hacked if connected to the internet.
In this article, I explore some of the common ways you could be hacked and how to prevent them from occurring.
Table of Contents
In summary, Home Assistant can be hacked if reasonable steps haven’t been followed to configure your system. You should always follow best practices, implement recommended settings and keep your software and device firmware up to date to reduce the chance of being hacked.
Over the years there have been occasional reports from various users of Home Assistant that they have been hacked. In all of these cases, it was down to them implementing bad security such as using weak or default passwords or exposing too many internal network ports to the internet.
Below you will discover the ways you could be hacked and I show you exactly what you need to do to keep Home Assistant as secure as possible.
How Secure Is Home Assistant against Hackers?
Home Assistant itself is a very secure piece of software but like any product, vulnerabilities can surface and Home Assistant is no exception to this. Since 2017 there have been 4 public vulnerabilities reported with a medium score of 5.0 or below. Each of these reported vulnerabilities can be found at https://www.cvedetails.com/vulnerability-list/vendor_id-17232/Home-assistant.html.
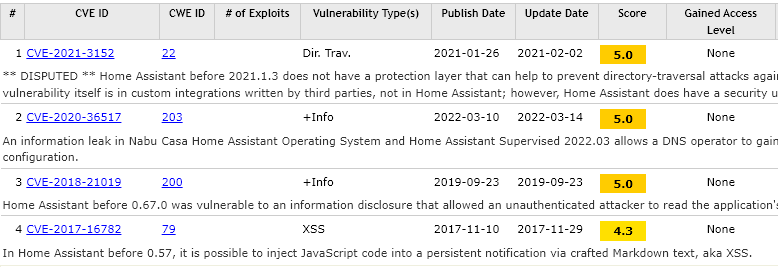
Most of the reported vulnerabilities were related to information disclosures and the most recent vulnerability was actually caused by a third-party add-on, and not Home Assistant itself.
How can Home Assistant be hacked?
Authentication Provider Configuration
One of the most common ways users can get hacked in Home Assistant is to expose their installation to the internet and not configure a password. Before version 0.90 of Home Assistant, it was possible to set up the “API Password” authentication provider without a password being set. Some users ended up getting caught out by this as they did not fully understand what they were doing. Eventually, the API Password value field was set as a required option in newer versions.
The API password authentication provider is now considered legacy and will be fully deprecated in future versions of Home Assistant.
Trusted Networks Configuration
Some users can also misconfigure the trusted networks’ authentication provider by allowing access to larger subnets. Any user connecting to Home Assistant from an IP address within the trusted network’s subnet can automatically authenticate without needing credentials.
It is critical that you only configure a single trusted proxy address and only include your local network subnet.
Remote Access Configuration
Exposing a Home Assistant server to the internet via DuckDNS and an Nginx reverse proxy is a hugely popular method of setting up remote access. When this is done your Home Assistant server can be found by anyone on the internet by using websites such as Shodan or CRT.SH.
This link will show you a list of Home Assistant servers it has recently discovered on the internet.
https://crt.sh/?q=homeassistant.%25
There’s no security through obscurity
Further examples that makes Home Assistant vulnerable to hackers
- Using default passwords or short and weak passwords
- Exposing internal network ports to the internet
- Not using HTTPS for inbound connections
- Not enabling two-factor authentication
Options to prevent hackers accessing Home Assistant
In the list below I outline three common approaches for setting up remote access to Home Assistant and ranked by security strength and convenience. The least convenient option provides the best security and also requires great technical knowledge to set up.
The best option for most people will be to use Nabu Casa which is both secure and easy to use, especially if you plan to integrate Google Assistant or Amazon Alexa.
1. Point-to-Point VPN and VLAN segregation
In this setup your Home Assistant server is not published directly to the open world, access to it is only allowed via your own VPN server. Inside your home network, all your IoT devices are completely separated from your main network of computers, storage devices, and servers. If an IoT device gets hacked into then the hacker should not be able to access your computers.
Most average homeowners are not going to follow this design as it not only requires in-depth knowledge of networking but also depends on owning specialist equipment to meet the requirements. You will need to know how to set up a secure VPN service and host it yourself, on top of this your network equipment will need to be able to support VLAN tagging for the segregation to work correctly.
Verdict: Most secure but the least convenient
2. Nabu Casa ($6.50 monthly subscription).
Nabu Casa is a subscription service created by the founder of Home Home Assistant. It allows you to set up remote access from anywhere in the world to your Home Assistant server easily and conveniently. Nabu Casa provides convenience because you do not require much technical knowledge in the configuration and it provides you with your own hostname and SSL certificate.
The second major benefit of using Nabu Casa is the ability for it to connect to your voice assistants. Currently, it supports either Google Home or Amazon Alexa. With this, you can control Home Assistant with your voice through smart speakers or from your Android phone.
Without Nabu Casa, it is possible to connect Home Assistant to your voice assistants but the setup process can be very tedious and requires your Home Assistant server to be exposed to the internet using a static hostname.
Verdict: Largely secure and generally convenient
3. DuckDNS Domain pointed to your Router / Home Assistant instance.
This setup is probably the most common as it can be easy to configure, has no additional costs, and doesn’t require any specialist hardware.
The general idea is you obtain a free subdomain from DuckDNS such as myhomeasstant.duckdns.org, integrate it with Let’s Encrypt for your free SSL certificate then set up an Nginx reverse proxy then open up a network port on your router to allow the traffic in.
The Home Assistant Add-on Store provides first-party add-ons for DuckDNS, Let’s Encrypt, and Nginx Reverse Proxy
Verdict: Not very secure but the most convenient
How can I prevent Home Assistant from being hacked?
Tips on keeping Home Assistant secure
- Always keep your device firmware up to date, consider doing a monthly review to check. Use the power of Home Assistant to set up sensors that alert you when new firmware and updates are available.
- Follow the advice given by Home Assistant by following their security checklist here https://www.home-assistant.io/docs/configuration/securing/
- Always use strong passwords and use a password manager to store them.
- Use the secrets file in Home Assistant to store passwords and keys
- Set up and use two-factor authentication
- Configure IP BANs on failed login attempts with the HTTP component
- Use VLANs to segregate your home network from your smart home devices
- Keep your phone secure if you have the Home Assistant companion app installed
- Be careful with exposing external door locks to voice assistants.
- Always use HTTPS for both inbound and outbound access.
Conclusion
Hopefully, you will have learned that Home Assistant itself is secure enough as a piece of software to use but that it also requires additional care from its users to keep it that way. Home Assistant has a great community via their official forums or on Reddit, if you are unsure about anything go and have a search around for the answers there or ask somebody for assistance.
Do you have any security tips that have not been mentioned? Share them with us on Twitter!

